Refactoring C codeError handling is HARD, error REPORTING is much harder
As part of my usual routine, I’m trying out writing some code in C, to get a feeling for a different environment. I wanted to build something that is both small enough to complete in a reasonable time and complex enough that it would allow to really explore how to use things. I decided to use C (not C++) because it is both familiar and drastically different from what I usually do. The project in question? Implementing the network protocol I wrote about here. Another part of the challenge that I set out to myself, this should be as production quality code as I could make it, which means paying all the usual taxes you would expect.
The first thing that I had to do was to figure out how to actually networking and SLL working in C. Something that would take me 5 minutes in C# took me a several hours of exploring and figuring things out. Eventually, I settled down on the obvious choice for SSL with OpenSSL. That is portable, reasonably well documented and seems fairly easy to get started with.
Here is some code from the sample TCP server from the OpenSSL documentation:
This is interesting, it show what needs to be done and does it quite clearly. Unfortunately, this isn’t production quality code, there are a lot of stuff here that can go wrong that we need to handle. Let’s wrap things in proper functions. The first thing to do is to capture the state of the connection (both its socket and the SSL context associated with it). I created a simple structure to hold that, and here is how I close it.
So far, pretty simple. However, take a look on the code that creates the connection:
As you can see, quite a lot of this function is error handling and cleanup. This code looks like it does the right thing and cleanup after itself in all cases. So far, so good, but we are still missing a very important component. We handled the error, but we haven’t reported it. In other words, from the outside, any failure will look exactly the same to the caller. That is not a good thing if you want to create software that is expressive and will tell you what is wrong so you can fix it.
If this was C#, I would be throwing an exception with the right message. As this is C, we run into some interesting issues. As part of your error handling, you might run into an error, after all… In particular, good error handling usually requires string formatting, and that can cause issues (for example, being unable to allocate memory). There is also the issue of who frees the memory allocated for errors, of course.
Typically, you’ll see code that either prints to the console or to a log file and it is usually a major PITA. OpenSSL uses a thread local error queue for this purpose, which gives you the ability to hold a context, but it requires an awful lot of ceremony to use and doesn’t seem to be useful for generic error handling. I decided to see if I can do a quick and dirty approach to the same problem, with something that is slightly more generic.
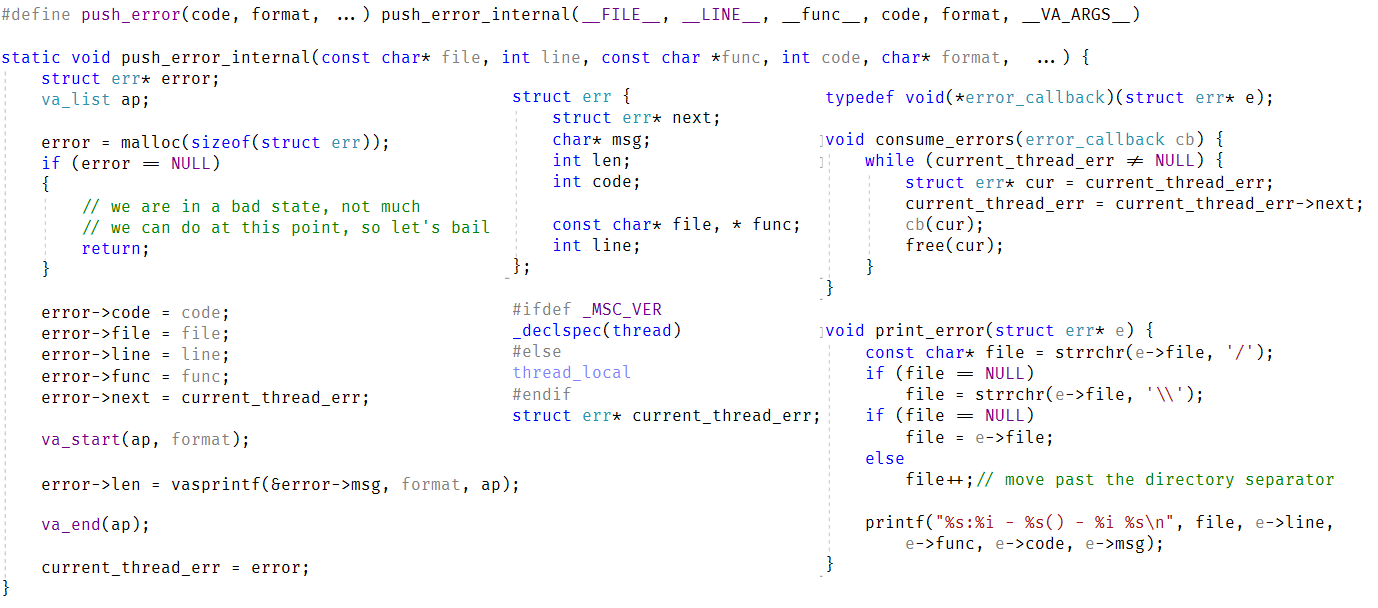
The purpose was to get reasonable error handling strategy without too much hassle. Here is what I came up with. This is a bit much, but I’ll explain it all in a bit.
Whenever we get an error, we can call push_error. Note that I included an error code there as well, in addition to the string. This is if there will be a need to do programtic error handling, for example, to handle a missing file that is reported “upstairs”.
I also included how we get errors out, which is pretty simple. You can figure out from here how you would handle error handling in code, I’m going to assume.
Here is how this is used:
And the output that this will print to the console would be:
consoleapplication4.cpp:211 - main() - 1065 can't open db: northwind
consoleapplication4.cpp:210 - main() - 2 cannot open file: raven.db
And yay, I invented exceptions!
Also, I have a memory leak there, can you find it?
More posts in "Refactoring C code" series:
- (12 Dec 2018) Going to async I/O
- (10 Dec 2018) Do we need a security review?
- (07 Dec 2018) Implementing parsing
- (04 Dec 2018) Multi platform and Valgrind
- (03 Dec 2018) Choosing the next direction
- (30 Nov 2018) Giving good SSL errors to your client…
- (29 Nov 2018) Starting with an API
- (27 Nov 2018) Error handling is HARD, error REPORTING is much harder










Comments
Vasprintf allocates a buffer.
You don’t show your cleanup code but I’m assuming you walk the list from current_thread_err freeing the next pointers?
Ah, just spotted your consume_errors function! It needs to deallocate the buffer allocated by vasprintf.
Is free the correct deallocator for that?
What C version do you use ?
Daniel, I believe that I'm using
C99, why?Hi, because I thought it was C11. Is it possible to run C11 in visual studio ?
Daniel, No, I don't believe so. They are mostly focused on C++, not C, I think.
threadlocaldoesn't work, for exampleOk, thanks for the information.
Comment preview